Key Takeaways
- VPN split tunneling enables the division of internet traffic for enhanced efficiency and flexibility.
- Users benefit from improved speed, optimized bandwidth, and better control over data flow.
- It’s essential to balance the advantages of split tunneling with potential security risks if improperly configured.
What is VPN Split Tunneling?
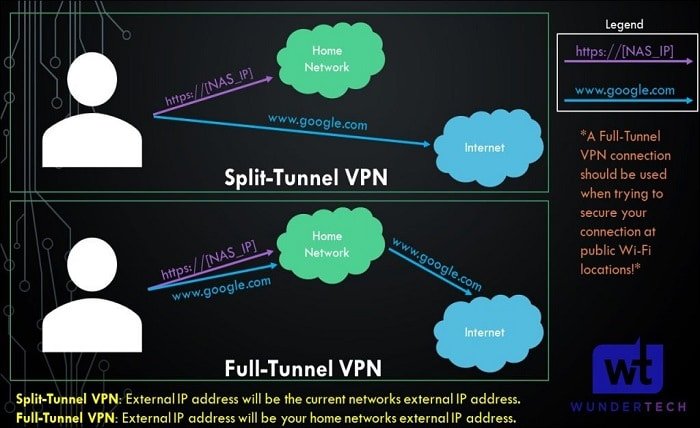
Maintaining a fast and efficient internet service is crucial in today’s hyper-connected world, where digital interactions are constant and business operations rely heavily on seamless connectivity. VPN split tunneling is a highly beneficial strategy for optimizing both performance and security in internet usage. Simply put, it allows users to selectively channel specific internet traffic through a VPN while routing other traffic directly to the internet. This partitioning facilitates a dual approach, ensuring that resources are allocated efficiently and securely.
The practical advantage of split tunneling VPN is its ability to prioritize different internet demands. This means users can manage and protect sensitive data through encryption while accessing less critical sites or applications more quickly by bypassing the VPN barrier. This flexibility is crucial in environments where security and speed demand high attention.
How VPN Split Tunneling Works
The underlying mechanics of split tunneling involve segmenting internet traffic into at least two channels. The first channel routes through a VPN service, providing the necessary encryption and security for sensitive data, while the second allows other data to take a direct path to the internet. This division lets users ascertain which traffic is crucial enough to warrant VPN protection and which is routine enough to proceed directly into the public domain.
This approach fortifies security where necessary and reduces the load on the VPN, mitigating potential bottlenecks and latency issues while preserving network resources for tasks that genuinely require encrypted routing. As the digital age progresses, tools like split-tunneling become integral to maintaining a robust and agile internet connection.
Benefits of Using VPN Split Tunneling
- Improved Speed:A configuration that allows non-essential traffic to bypass a VPN increases speed, causing less lag during internet usage. This acceleration is particularly noticeable when accessing media-rich content or engaging in high-bandwidth applications, as bypassing unnecessary encryption frees up processing capacity.
- Bandwidth Optimization:Split tunneling ensures bandwidth is utilized more judiciously by intelligently routing traffic. Prioritizing essential tasks for the VPN means critical applications receive the bandwidth they need, while less essential processes don’t unnecessarily consume network resources. This improves overall network efficiency and performance.
- Flexibility:Split tunneling offers flexibility that aligns directly with the user’s immediate needs. It allows real-time customization of internet traffic based on current priorities. Whether the focus is on security for sensitive transactions or speed for general tasks, users can shift their traffic flow accordingly without compromising on either front.
Security Aspects to Consider
While VPN split tunneling offers noteworthy benefits, it is crucial to approach its implementation with a keen understanding of security implications. Traffic bypassing the VPN does not benefit from the security features VPNs provide, such as data encryption. This creates a risk of exposure to cyber threats. Therefore, users must carefully consider which applications and tasks are safe to route outside the VPN.
Organizations are advised to conduct a comprehensive evaluation of their security requirements. This might involve implementing split tunneling for specific trusted applications while maintaining complete VPN protection for sensitive operations requiring confidentiality, such as internal communications or sensitive financial transactions.
Real-World Applications of Split Tunneling
In practice, many enterprises find the strategic deployment of VPN split tunneling a practical solution for the modern workplace, especially with the increasing prevalence of remote work. It effectively supports productivity by allowing employees to access essential web resources optimally without compromising secure access to sensitive corporate data. For example, while cloud-based applications or large downloads might proceed directly to maintain speed, sensitive data exchanges would prioritize VPN encryption.
This method is beneficial not only for corporations but also for individual users who need to juggle multiple workstreams. It ensures secure connections where necessary and fast access elsewhere. As businesses strive for efficiency, split tunneling becomes essential in the digital workspace toolkit.
Setting Up VPN Split Tunneling
To set up split tunneling, users must familiarize themselves with their VPN client’s capabilities and specific networking requirements. While the setup may seem daunting initially, many VPN service providers offer simple-to-follow guidelines or built-in tools dedicated to split tunneling. Setting parameters based on users’ networking preferences can ensure seamless integration. Guidance on choosing and configuring the appropriate VPN service is understandably crucial, as detailed in resources like this guide.
Users should thoroughly understand the implications of routing specific traffic outside the encrypted VPN. Testing and reviewing different configurations helps them discover the optimal setup for their internet usage needs.
Potential Drawbacks and Challenges
Despite the enhanced speed and preserved bandwidth benefits, VPN split tunneling has potential downsides. The primary concern is security vulnerabilities that could arise if critical data is unintentionally routed outside the protected VPN environment. Thus, users should only deploy split tunneling when routing traffic directly over the Internet to ensure safety.
Users must balance convenience and security, continuously monitoring the split tunneling configuration to realign it with new security needs and emerging threats. Organizations should implement best practices and policies to ensure the configurations are secure, adequate, and aligned with industry standards to mitigate risks.
Conclusion: Is VPN Split Tunneling Right for You?
Ultimately, the decision to utilize VPN split tunneling revolves around assessing specific user needs, the importance of speed versus security, and the particular applications involved. Those who require efficient management of their online activities without diluting critical security features will find split tunneling highly advantageous. The ability to toggle between a fast, direct internet connection and a secure, VPN-protected pathway offers users the flexibility to tailor their online ecosystem efficiently.
Consider exploring VPN topics in further detail to understand better their ubiquitous role and indispensable nature in protecting online interactions. As this landscape evolves, split tunneling remains a pivotal tool for those seeking to maximize security and internet performance.